Grandstream VoIP over OpenVPN
asterisk, gxp1625, vpn, settings, config, nat
Grandstream VoIP telephones are very popular because of their high build quality compared to an excellent price. In some cases you want to use an encrypted communication channel between your device and the PBX (e.g. asterisk). The current grandstream firmware includes basic OpenVPN support (client mode, tun) which allows you to tunnel the whole SIP/RTP traffic over an encrypted channel. This is also the best solution to avoid any kind of NAT/routing issues because all devices are directly accessible within the virtual ip subnet.
OpenVPN Server Config#
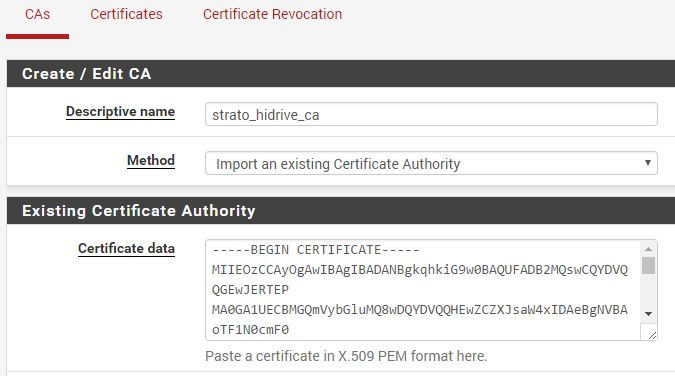
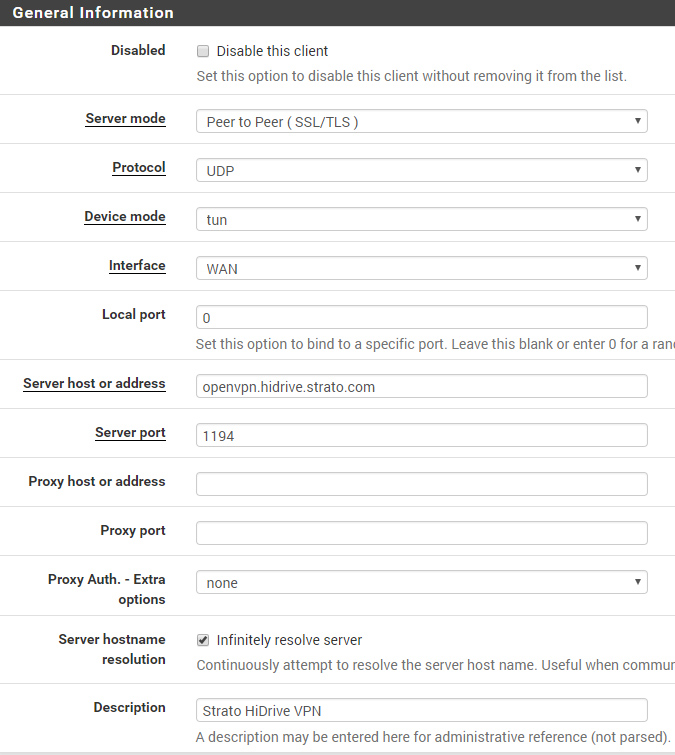
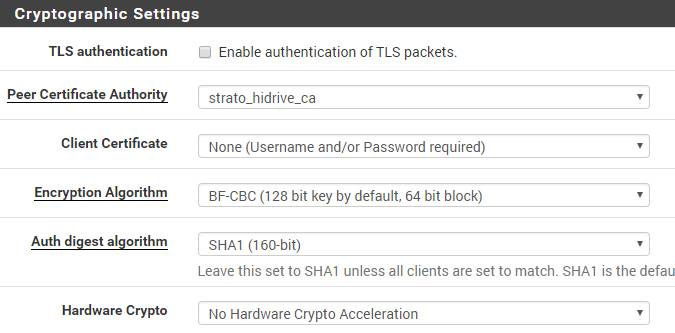
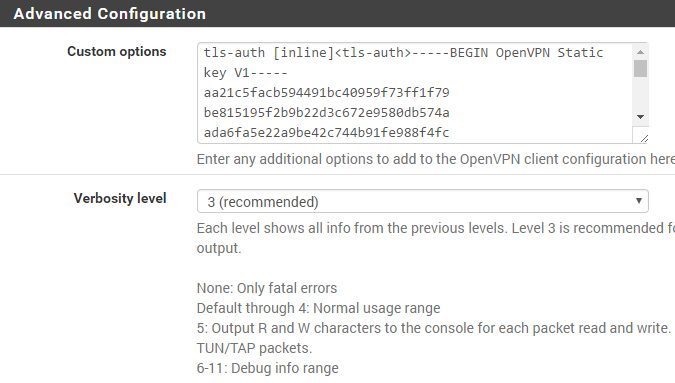
Use the following (minimal) configuration as template. The important options are set to work with the current grandstream firmware (1.0.4.106). Certificate based authentication is preferred for security (login/password not needed)!
tls-server dev tunX topology subnet server 172.16.1.0 255.255.255.0 port 10111 proto udp # cert based auth pkcs12 server.p12 # 1024 and 2048 bit dh params are supported dh dh2048.pem keepalive 10 120 script-security 2 # bh-cbc as well as aes-128-cbc are supported by the current firmware cipher aes-256-cbc # well sha1 is a bit weak but its set within grandstream firmware auth sha1 # compression has to be enabled comp-lzo tun-mtu 1500 mtu-disc yes # custom logging verb 3 # retain TOS flags (VoIP) passtos # internal network (VOIP Server) push "route 10.16.0.1 255.255.255.0"
Notes#
- Don’t forget to alter your firewall rules. The new OpenVPN subnet needs to be accessible by your VoIP Server (e.g. asterisk) and vice versa
- Add Quality-of-Service rules to your router which matches the OpenVPN port set above. The traffic should be marked with class EF (realtime, expected forwarding) to avoid package lost. Default VoIP rules will not match because of the encrypted channel!